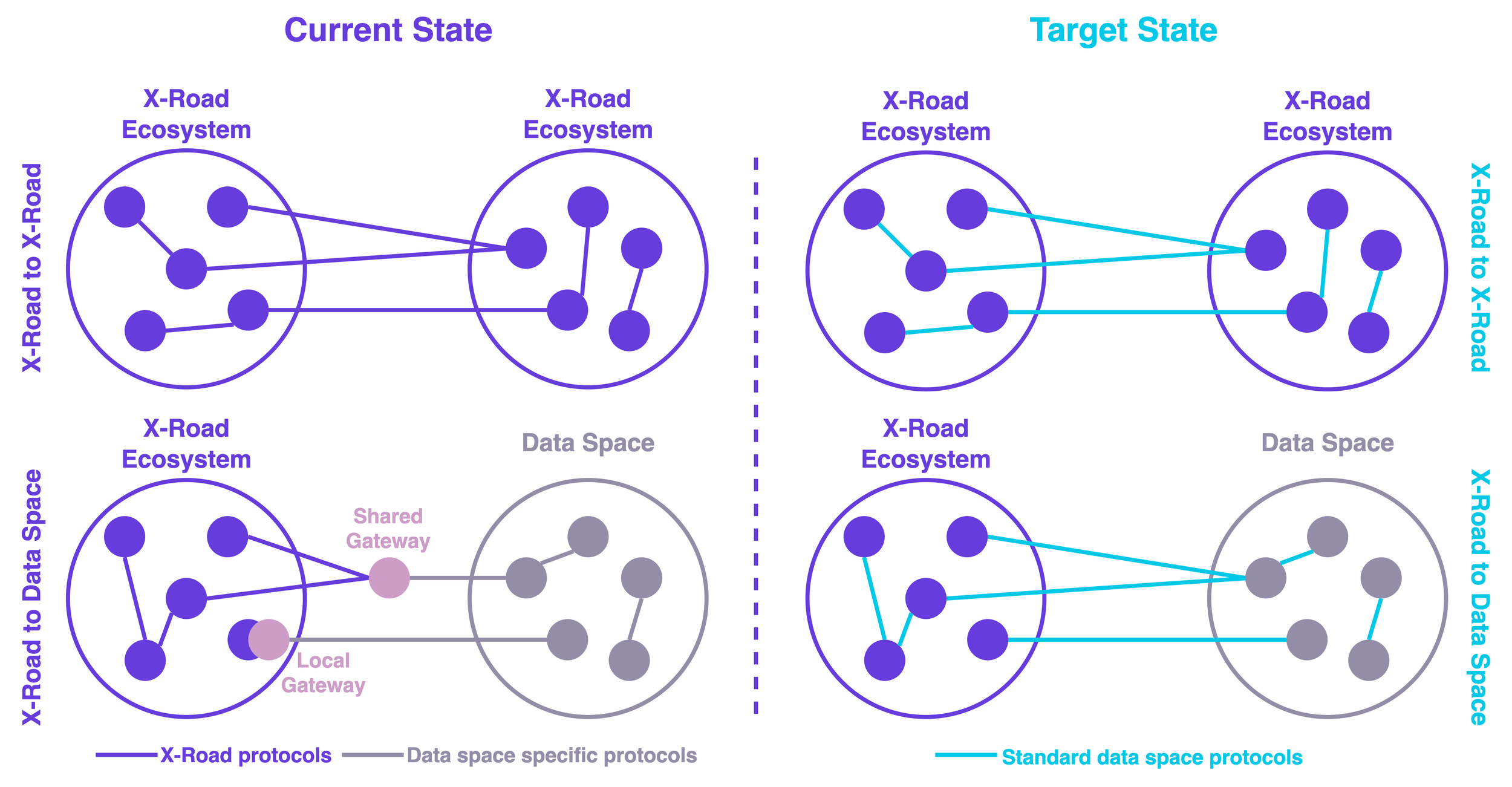
During the second half of 2024, the X-Road 8 “Spaceship” development continued nonstop after the initial proof of concept (PoC) was completed at the end of May. At the beginning of the PoC project, the main question was: Can X-Road be transformed into a data space technology in a backwards-compatible manner? Based on the outcome, the short answer was yes.
In practice, the answer means that the PoC project didn't discover any significant roadblocks that would make reaching the goal impossible. Instead, it discovered many questions and areas that require further investigation. Since completing the project at the end of May, we have continued to work with the identified questions and challenges and dig deeper into various areas of the implementation.
In this blog post, we explore what has happened after completing the initial PoC project at the end of May.
Changes to the X-Road architecture
X-Road 8 will provide improved cloud compatibility and make using X-Road easier in the cloud. In practice, X-Road 8 will be designed and built to leverage the capabilities and advantages of cloud computing environments. X-Road 8 will be built to run in cloud infrastructures and take advantage of cloud platforms' scalability, flexibility, and resilience. For example, it supports scaling the Security Server on a module level (e.g., signer, proxy) and enables the use of services offered by cloud platforms (e.g., secret storage, configuration management). These goals can only be achieved with changes to the X-Road's architecture.
The aim is to make X-Road more modular so that different modules can be deployed on separate hosts (or containers) and scaled independently. X-Road’s modules are made more loosely coupled, isolated, and configurable to enable this. For example, on a more concrete level:
Different modules communicate with each other over gRPC interfaces rather than sharing the same data files on the file system.
Enable the use of external configuration management services instead of storing configuration files locally on the Security Server.
Migrate configuration from ini files to yaml files.
Instead of hardcoding the location of other modules in the source code, it's possible to configure each module's address using configuration properties.
Some changes may already be introduced in X-Road 7, and they don't affect existing users. For example, make some currently hard-coded configuration items configurable using the current hard-coded values as defaults.
Better support for containers
In X-Road 7, the Security Server already supports containerised deployment, but the current implementation has certain limitations. For example, all the Security Server modules are deployed to a single container, and splitting them up into multiple containers is not supported.
In X-Road 8, different Security Server modules will be deployed to separate containers, enabling more flexible deployment and scalability options. For example, scaling out can be implemented by scaling out an individual module causing a bottleneck rather than scaling out the whole Security Server instance.
Although X-Road 8 has made great efforts to provide better support for cloud platforms and containers, it will continue to support the current native Linux-based (Ubuntu + RHEL) deployment options. Therefore, users are not forced to migrate to the cloud and/or containers when upgrading to X-Road 8.
New modules for the Central Server and the Security Server
Designing and implementing the X-Road 8 architecture is still a work in progress, and further changes are to be expected, but some new modules have already been implemented. However, the implementation of the new modules has yet to be on a production level, and some of them have been implemented as mock services. Nevertheless, here's a more detailed description of the new Central Server and Security Server modules.
The new Central Server modules are:
Catalog Service (xroad-ds-catalog-service)
Collects service metadata in Data Catalog Vocabulary (DCAT) format from Security Servers, stores it centrally and provides an API to query the metadata. Similar to the existing X-Road Catalog extension, but the implementation is based on different metadata standards and protocol specifications.
Credential Service (xroad-ds-credential-service)
Issues X-Road compliance (and other) credentials to X-Road member organisations. The credentials are based on the W3C Verified Credentials Data Model v2.0 specification.
Identity Hub (xroad-ds-identity-hub)
Hosts X-Road Operator’s DID document and stores verifiable credentials. Implements the Decentralised Claims Protocol (DCP) specification.
Secret storage (xroad-secret-store-<local|remote>)
Secure storage to store application secrets, e.g., gRPC keys and certificates. Uses a local or remote installation of the OpenBao open-source product.
The new Security Server modules are:
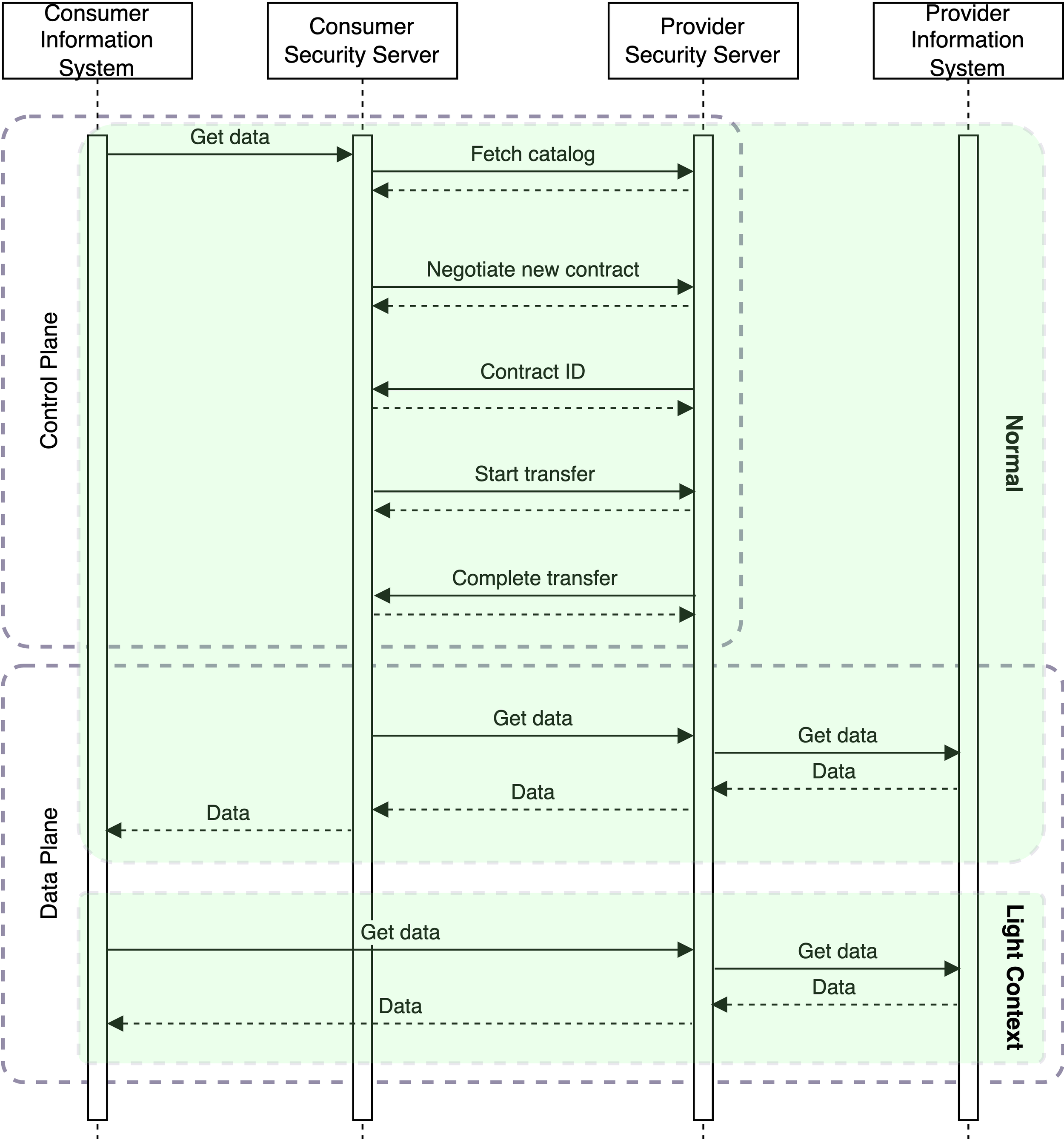
Control Plane (xroad-ds-control-plane)
Service discovery and contract negotiation. Implements the Data Space Protocol (DSP) specification.
Data Plane (xroad-ds-data-plane)
Actual data transfer based on the X-Road Message Transport Protocol.
Identity Hub (xroad-ds-identity-hub)
Hosts X-Road member organisations’ DID documents and stores their verifiable credentials. Implements the Decentralised Claims Protocol (DCP).
Secret storage (xroad-secret-store-<local|remote>)
Secure storage to store application secrets, e.g., gRPC keys and certificates. Uses a local or remote installation of the OpenBao open-source product.
Changes to message signatures
X-Road 7 uses batch signatures to sign all the messages exchanged between X-Road member organisations. The Security Server is responsible for producing and verifying the signatures and logging the messages. Batch signatures perform better than non-batch signatures, but the downside is that they do not fully conform to the eIDAS technical specifications. Therefore, X-Road 8 will support fully eIDAS conformant non-batch signatures and batch signatures. Also, X-Road 8 will support fully eIDAS-conformant ASIC-E containers for archiving the message logs.
Supporting non-batch signatures in X-Road 8 requires changes to X-Road 7 to guarantee interoperability between the two major versions. In other words, backwards compatibility requires adding partial support for non-batch signatures in X-Road 7. In practice, version 7 Security Server must be able to verify non-batch signatures and log all the message parts included in the signature. The required changes are implemented in X-Road version 7.6.0 and don't affect the behaviour or performance of X-Road 7 Security Servers. Thanks to the changes, X-Road 8 will be backwards compatible with X-Road 7 starting from version 7.6.0.
Trust framework
Currently, the X-Road trust framework is based on X.509 certificates. Instead, many data space initiatives, including Gaia-X, are basing their trust frameworks on W3C Verified Credentials (VC) and W3C Decentralised Identifiers (DID). In addition, a couple of alternative protocols define how credentials are exchanged between various data space components in different interactions.
Since being technically interoperable with Gaia-X is in X-Road 8's scope, X-Road 8 must also support the aforementioned technologies. Instead of supporting multiple trust framework technology stacks in parallel, it's more efficient to try to limit and streamline the number of used technologies. Therefore, we've been looking into migrating the X-Road trust framework from X.509 certificates to VCs and DIDs.
So far, we have implemented an experimental X-Road member credential that can be used to prove that an organisation is a member of a specific X-Road ecosystem. The X-Road operator issues the credential when a new member joins the X-Road ecosystem. Nevertheless, every member organisation still needs a sign certificate issued by a trusted Certificate Authority (CA) since the X-Road member identifier in the credential must match the member identifier in the sign certificate. Also, every member still needs to be able to sign their messages, which is why the sign certificate is still required. Instead, the credential can be used to authenticate members during data transactions and control access to services.
At first glance, the X-Road member credential doesn’t provide much new compared to the existing sign certificate. However, the data space protocol stack is leaning towards credentials, which is why X-Road 8 should also support them. In addition, supporting credentials opens many new opportunities for X-Road. The use of credentials doesn't have to be limited to the X-Road member credential, and there could be various other credentials, too.
For example, the X-Road operator could conduct automated port scanning of all the Security Servers registered in the ecosystem and issue a security credential to every Security Server that meets the security requirements. In this way, X-Road member organisations could prove to other members that their Security Server meets the security requirements of the ecosystem and that information could be utilised when granting access to services. In addition, credentials could also be issued by other parties and not just the X-Road operator, which increases the number of possibilities significantly.
What’s next?
During the second half of 2024, the main focus of X-Road 8 development activities was X-Road-related topics. In addition, we are continuously working with the Eclipse Dataspace Components (EDC). Still, the work is more about better integrating the EDC into X-Road, utilising its extensibility and applying its concepts rather than working on implementing the Data Space Protocol (DSP) or the Decentralised Claims Protocol (DCP). When it comes to implementing the data space protocol stack, X-Road is utilising the implementation coming from the EDC master repository. Also, we’re continuously evaluating the development of the data space protocol stack and considering available options for the different layers of the stack. For example, on the trust layer, X-Road is currently using the DSP, but we’re also looking into OpenID for Verifiable Credentials (OID4VC) as a potential alternative.
Many of the topics discussed in this blog post are very complex and wide, and therefore, we will continue to work on them in the near future. None of the areas have a production-level implementation available yet, so there's still plenty of work to be done. Also, there are several areas that we haven’t even looked into yet, e.g., federation, operational, and environmental monitoring.
The changes in X-Road 8 are not limited to protocols and technical changes under the hood. Instead, the Central Server and Security Server UIs will be updated, too. The main logic of the UIs will remain the same, but they will have a new look and feel aligned with the X-Road 8 "Spaceship" visual style. The new UIs will probably be introduced when the X-Road 8 beta version is published in 2025.
More blog posts about X-Road 8 will follow in 2025. Stay tuned!